About us
-
About us
-
News
Service
-
Smart Service
-
Service Solutions
Data Center Full-Stack IT Architecture Integration
Infrastructure Operations Insight Analysis and Optimization
Business Migration To A Hybrid Cloud Environment
IT Infrastructure O&M Services For Chinese Enterprises Going Global
IT On-site Services For Multi-Branch Organizations
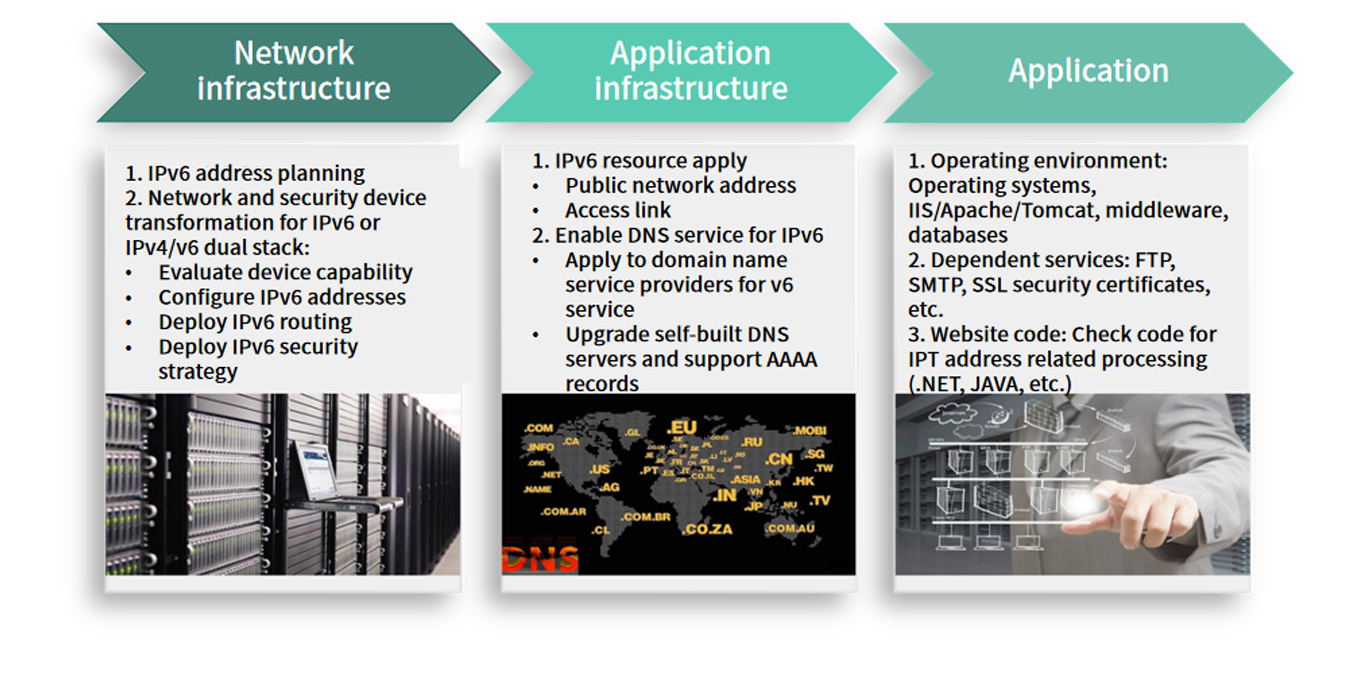
Enterprise IPv6 Application Transformation Consulting And Implementation
-
MSS
-
Smart Cloud Services
-
Security Services
-
海外服务en